Digital Forensics deals with finding out details on who was responsible for cyber crime activity, breach of systems or intrusions. Process includes getting digital devices from crime scenes and analyzing them in lab. In between this, there are lots of work to be done.
The process of working on a digital forensics case include : creating disk image (copies of the original suspect’s drive/device), hashing or verifying the integrity of the disk image, write blocking the disk image (setting it to read-only to verify disk image integrity), and analyzing the drive and its contents.
Digital Forensics 0x1a : Intro & FTK Imager Lab
Now, in this tutorial, let me create a image of local drive using software FTK Imager. We’ll create an exact replica of a local drive (F: Cybrary) that will be used in the scope of a digital forensic investigation, later.
Download and install free version of FTK imager and we are ready to go.
Assuming you have installed FTK imager, follow these steps.
- Launch FTK Imager by clicking on the ‘AccessData FTK Imager’ icon.
- Click File and look over the various options for creating images. We’ll be using the ‘Create Disk Image’ option. It’s good to note that you can also capture from memory, and image individual items.
- Select the desired drive in the resulting ‘Select Drive’ window. In this case, the drive we wish to image is ‘F: Cybrary’. Click Finish.
- The ‘Create Image’ window will appear. Note that the appropriate Image Source has been selected. Click Add to select the image type and choose the Image Destination.
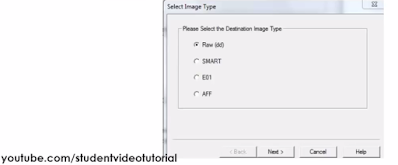
- Select the desired image format. We’ll be using dd. dd (disk dump) is the raw image file format. It’s used not only in Windows, but also in Linux. Select ‘Raw (dd)’ and click Next.
- Now, give case or evidence information in detail. This will help manage and track everything later on.
- Select the folder in which the image file will be placed (H: BJ). Also, give the image file a specific name if desired. Click Finish.
- Note that the image destination has been changed to H:. The disk image will be saved to the BJ Drive. Note: the disk image will be created in raw/dd. Make sure that ‘Verify images after they are created’ is checked – this will automatically create a hash for the image. The hash is used to verify that no changes have been made to the image file. Click Start to create the image file.
do not worry about blue line. line hides outdated info.
- The image will be created. This may take some time depending on the file size.
- The following window will appear once the image has been completed. Note that both an MD5 and SHA1 hash have been created and verified. The hash is the fingerprint of the disk image. If the disk image is altered, the hash values will change. Keeping track of these hashes will allow you to continually verify the hash of the image file during your investigative process. Any other investigator should be able to replicate this hash; this maintains integrity in the eyes of the court.
- Click on ‘Image Summary’ to view the following results pertaining to the image that has just been created. This information should verify what was entered in the creation process. It will also verify the created hashes. Also, for your reference, this information has been printed out into a text file in the location to which the image file was saved.
- Note that the image file (Thanks Cybrary.001) as well as the image summary file from above (Thanks Cybrary.001.txt) have been saved onto the ‘H: BJ Drive’. The .001 extension may be left as is, or can be changed to .dd. The .001 extension is used due to the fact that many times the file to be imaged is very large and must be split into multiple chunks. In that case, you would have Thanks Cybrary.001, Thanks Cybrary.002, etc.
I want to thank following 3 (references): nest.unm, Cybrary.it, OTW null-byte wonder how to
My this article is also published on Cybrary Op3n Content.












Comments
Post a Comment